Which of the Following Is Not a Valid Biometric Disadvantage
Bioelectrical Impedance Analysis BIA is able to make an estimation of body composition eg. Start studying Fundamentals of Network Security Chapter 11.

Blank Award Certificate Templates Word Awesome Free Certificate Template Certificat Free Certificate Templates Birth Certificate Template Certificate Templates
Biometric devices especially fingerprint scanners since theyre the most used amongst companies were found interesting by companies because they have many advantages.
. It is expensive and cannot be afforded by severalorganizations. This is possible simply because different bodily tissues eg. Biometric systems allows for greater accuracy and reliability in user authentication.
The palm and hand biometric techniques lack uniqueness in the geometry data. Though considered a natural and friendly. Disadvantages of biometric authentication.
It needs a new network configuration of the entire infrastructure. Here are some key points to consider regarding the disadvantages of biometrics. These factors include the enrollment time and the throughput rate but not acceptability.
In face biometrics a reader analyzes the images captured for general facial characteristics. Learn vocabulary terms and more with flashcards games and other study tools. Which of the following is a disadvantage of using biometric identification.
Ironically it also becomes the most dreadful disadvantage if biometric identifiers are stolen. Despite increased security efficiency and convenience biometric authentication and its uses in modern-day tech and digital applications also has disadvantages. Increased system sensitivity can cause a higher false rejection rate.
False acceptance rate is also known as Type II error. Answer C is incorrect because the FRR is separate from the False Acceptance Rate FAR. It needs a new network configuration of the entire infrastructure.
Data breaches Biometric databases can still be hacked. Different biometric technologies need. Start studying System Security 9-12.
First of all theyre cheap. Most of the biometric modalities work with physical traits such as fingerprint iris palm vein etc. Costs Significant investment needed in biometrics for security.
Environment and usage can affect measurements. Answer B is incorrect because valid users who are denied access may attempt to bypass or subvert the authentication system because they believe it does not work correctly. Security Guide to Network Security Ch 6 - 15.
A low enrollment time d. These factors do not include the enrollment time the throughput rate and acceptability. Require integration andor additional hardware.
It breaks the several firewall security rules. When combined with the use of a PIN it can provide two factors authentication. Quantities of fat mass and fat-free mass by running a small electrical current through the body.
For as long as it appears on the device. You may want to know the disadvantages of biometrics technology. Biometrics are great but its not always clear whether a given implementation is secure.
Various forms of biometric authentication include face voice eye hand signature and fingerprint each have their own advantages and disadvantages. Second they provide more security. Muscle fat bone etc all have varying amounts of water content and as a result they.
In this paper we discuss multi-factor biometric systems the di erent levels of fusion their advantages privacy and security issues associated with biometrics. Invasion of privacy b. The crossover error rate is the point at which false rejection rate equals the false acceptance rate.
A moderate degree of physical discomfort. Like all technology however biometrics also comes with some disadvantages. Systems are not 100 accurate.
Learn vocabulary terms and more with flashcards games and other study tools. Which of the following statements pertaining to biometrics is FALSE. Get Quizlets official Security - 1043 terms 722 practice questions 2 full practice tests.
Noise in sensed data- The accuracy play a major role in recognition of biometrics. Unlike PINs or passwords that can be changed if compromised biometric identifiers of a person cannot be changed if stolen. Which of the following is a disadvantage of using biometric identification.
It breaks the several firewall security rules. Cannot be reset once compromised. It can be faked and will not be trusted by several organizations.
One disadvantage of biometrics is cost. Creating a pattern of where a user accessed a remote web account is an example of which of the following. The accuracy of the biometric system is very sensitive to the quality of the biometric input and the noise present in the data will result in a significant reduction in the accuracy.
We are always looking for. 1 Introduction There are many issues regarding security and access control. Which of the following does not represent a reason a biometric device would be rejected by a majority of users.
In addition to the accuracy of the biometric systems there are other factors that must also be considered. Biometric the main disadvantage of face recognition is the lack of uniqueness which means that people looking alike can fool the. Biometric characteristics are permanent and this fact is one of the founding stones of biometric identification.
Physical Traits are not Changeable. Disadvantages of biometric systems. A high level of invasiveness c.
Cannot be forgotten or lost. If a system has a high FRR many valid users will be denied access. Biometric systems are often affected by the following problems 4.
And since all businesses seek minimizing cost they were attracted by those devices. What is a disadvantage or biometric readers. It is expensive and cannot be afforded by several organizations.
In this article Duo looks at what properties of biometrics make them good or bad at defending against one threat but not another then takes a deeper look at different fingerprint facial identification and vein scanning technologies and what makes them strong or weak. It can be faked and will not be trusted by several organizations. A TOTP token code is generally valid for what period of time.
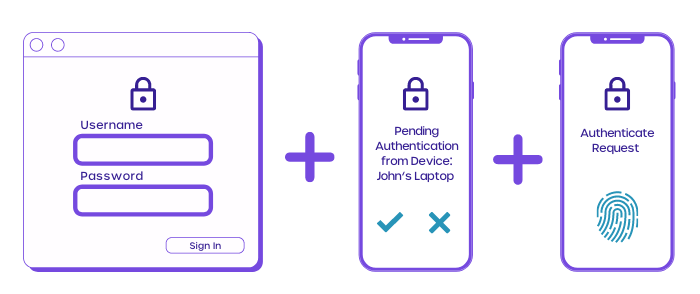
What Is Multi Factor Authentication And How To Enable Mfa Using Cyvatar

Virtual Exams Has Covid 19 Provided The Impetus To Change Assessment Methods In Medicine Bone Joint Open

4 Drawbacks Of Biometric Authentication

Sensors Free Full Text Imsc Eiotd Identity Management And Secure Communication For Edge Iot Devices Html
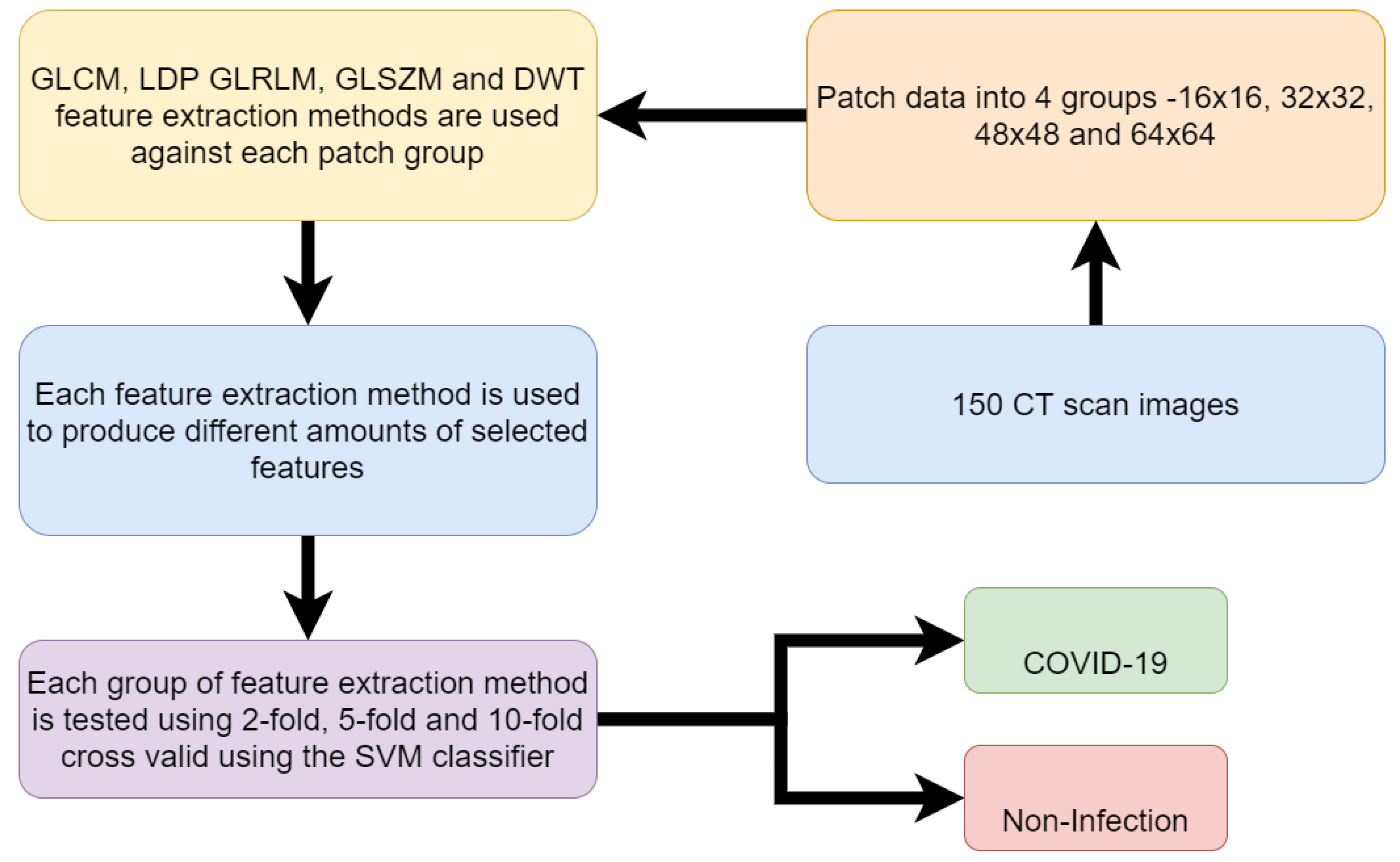
Sensors Free Full Text A Review Of The State Of The Art In Non Contact Sensing For Covid 19 Html

Electronics Free Full Text Securing Remote Access To Information Systems Of Critical Infrastructure Using Two Factor Authentication Html

5 Reasons To Use Biometrics For Multi Factor Authentication Id R D
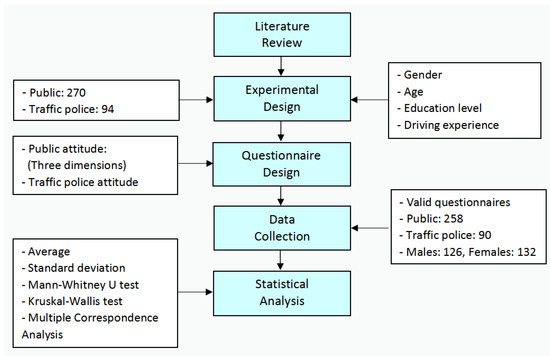
Applied Sciences Free Full Text Attitudes Toward Applying Facial Recognition Technology For Red Light Running By E Bikers A Case Study In Fuzhou China Html
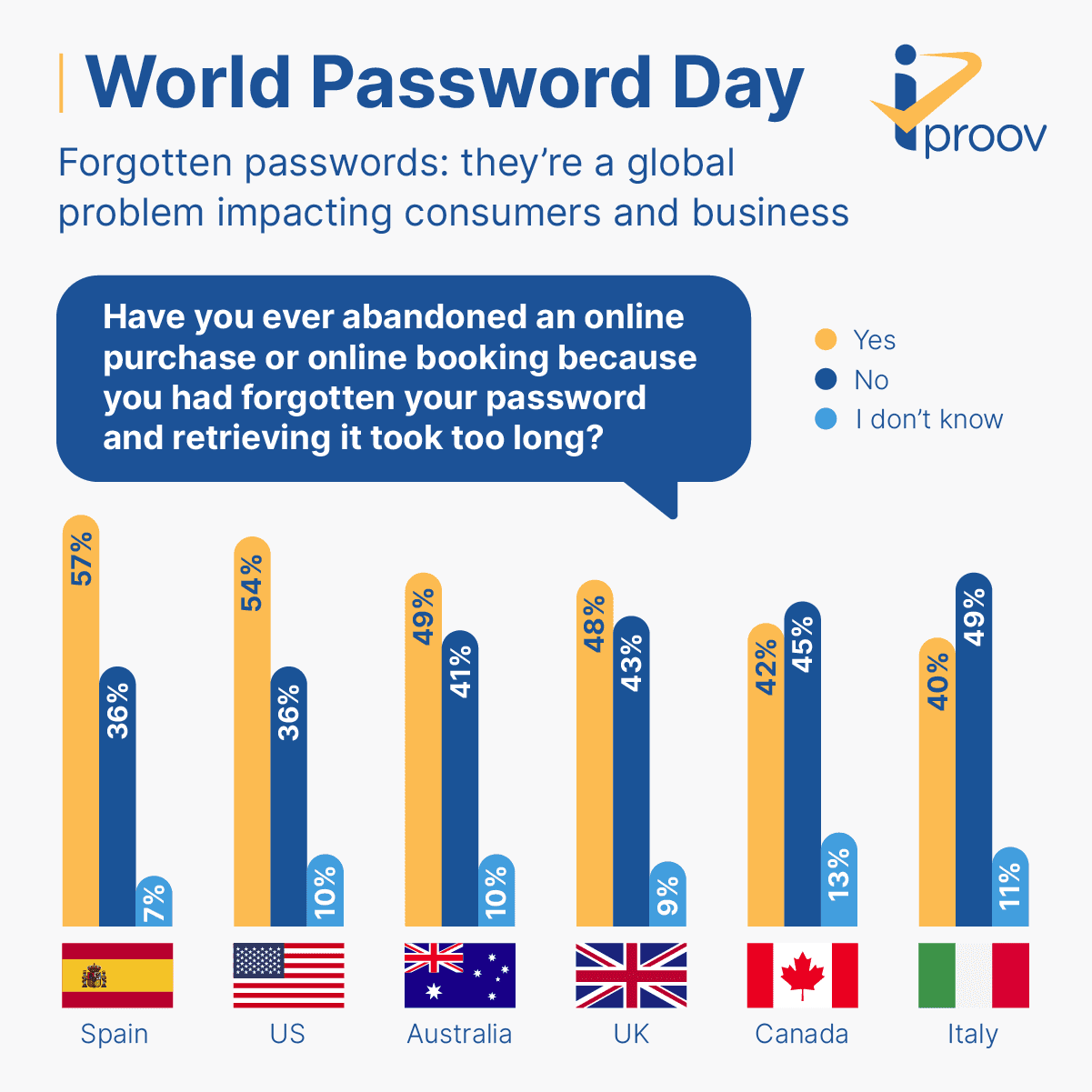
The Disadvantages And Problems With Passwords Iproov

Why Browser Fingerprinting Is Creating Challenges For Identity Security Secureauth

Data Free Full Text Information Quality Assessment For Data Fusion Systems Html

Iproov Launches The Biometric Authentication For Dummies Guide Iproov
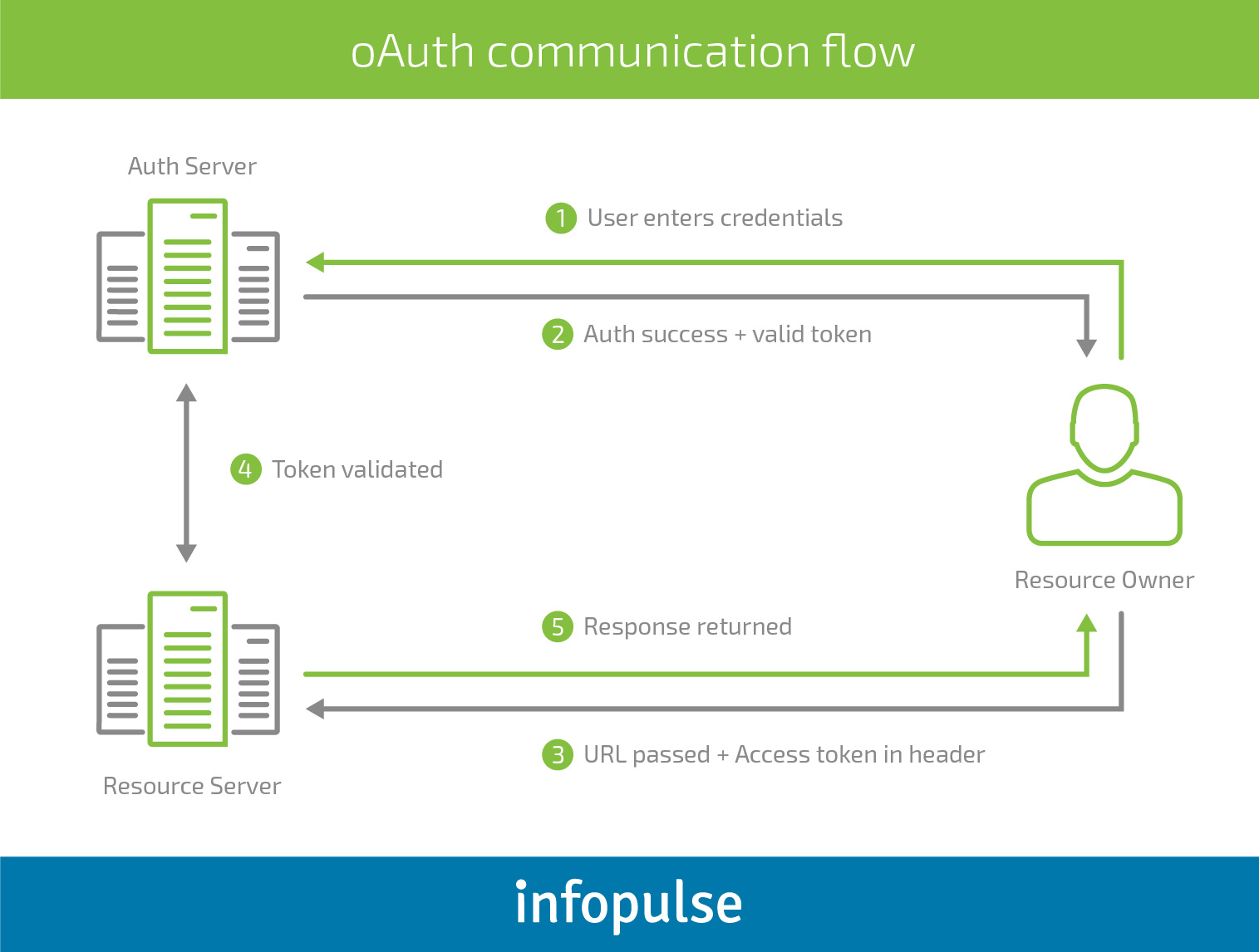
How To Enable Secure Authentication In Mobile Applications Mobile App Authentication Infopulse
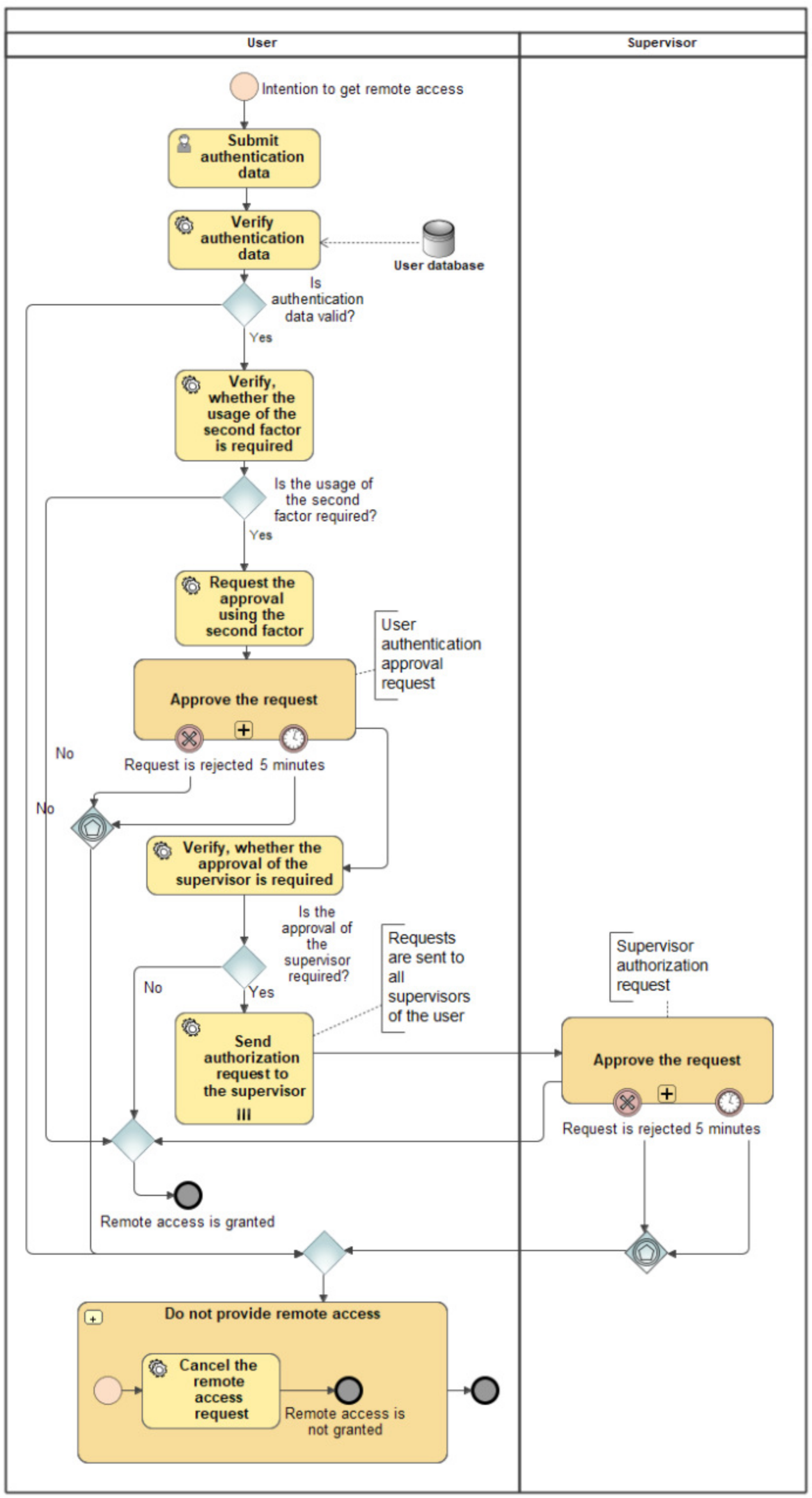
Electronics Free Full Text Securing Remote Access To Information Systems Of Critical Infrastructure Using Two Factor Authentication Html
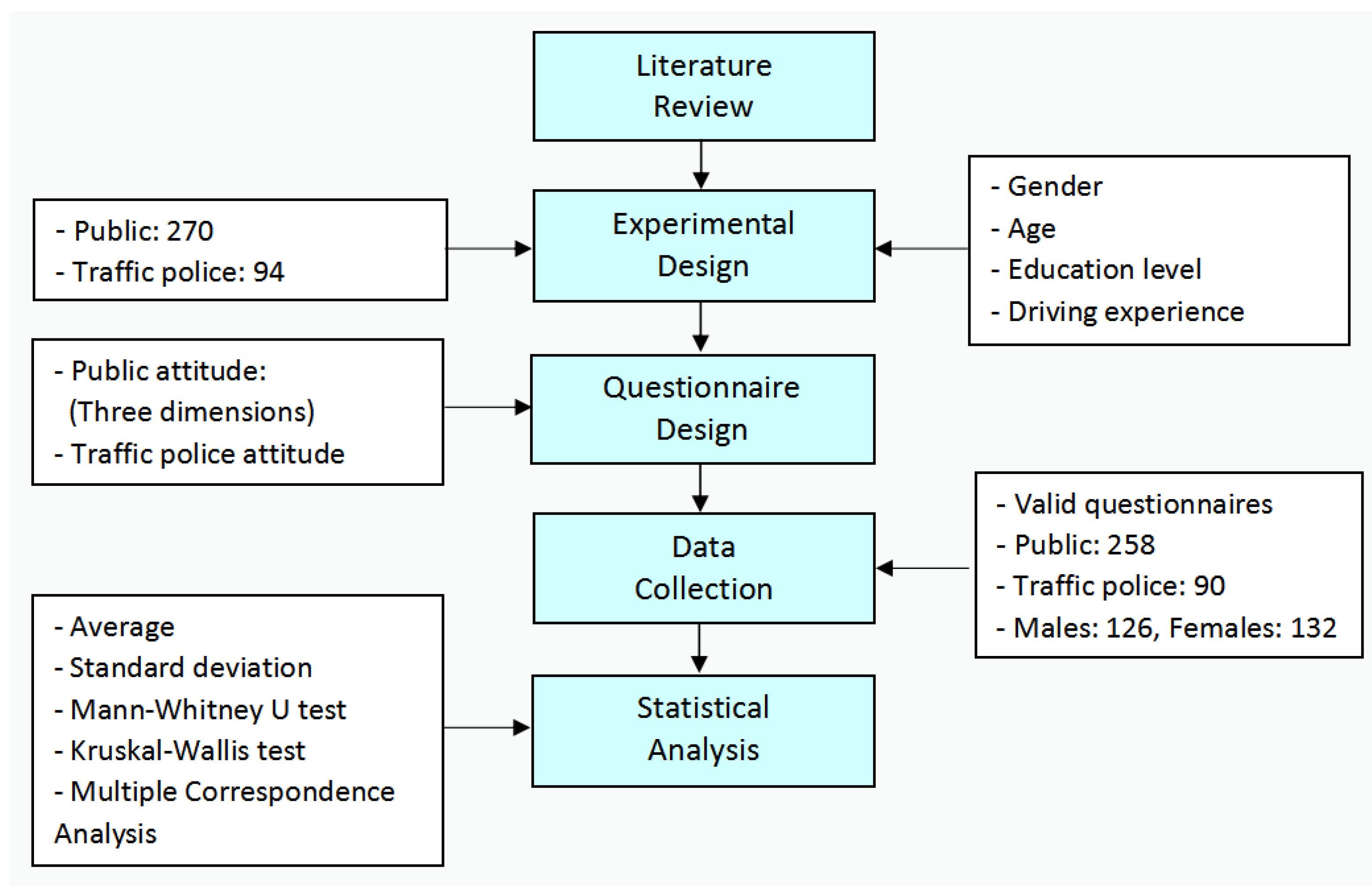
Applied Sciences Free Full Text Attitudes Toward Applying Facial Recognition Technology For Red Light Running By E Bikers A Case Study In Fuzhou China Html

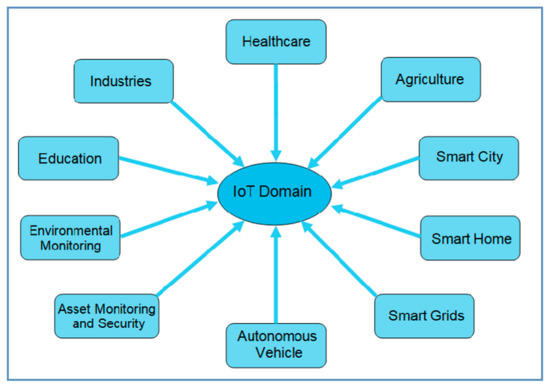
How To Pave The Way To Manageable Global Iot Deployments With Multi Imsi Sims
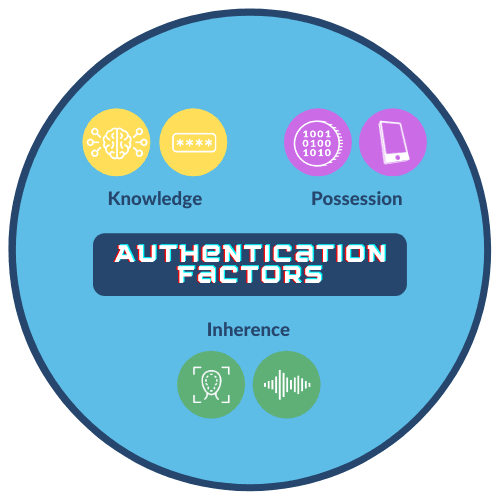
5 Reasons To Use Biometrics For Multi Factor Authentication Id R D


Comments
Post a Comment